
The growing acceptance and use of cloud services over the past few years shows that their advantages (such as scalability and elasticity, billing based on actual usage, worldwide availability) are slowly but surely becoming established in almost all companies and public authorities.
At the same time, the security risks of the cloud, such as shadow IT, uncontrolled data outflow (cloud-to-cloud communication), compromised cloud accounts, company data from the cloud on employees’ personal devices or even data protection violations, are real dangers that must be adequately addressed.
In any case, the first step towards secure use of the cloud is to create a cloud policy. Which applications and data can be stored in the cloud at all? What criteria are used to decide between on-premise and cloud? What exactly does the migration process look like? Which security controls are mandatory in the cloud and which are optional?
Two main problems: shadow IT and data outflow
In the second step, every company should get an idea of the actual, current cloud usage, and thus also of the existing extent of shadow IT. In this regard, manufacturers such as McAfee offer the option of an audit in which proxy logs are systematically evaluated for cloud use over the course of a month. The estimated 50 or so cloud services quickly become 900 or even 1,500 actually used cloud services in reality. A shadow IT audit results in a number of standard measures, such as completely blocking all high-risk cloud services to minimise risk, or consolidating dozens of cloud storage solutions into one or two secure standard providers. In this context, employees should also be made aware of and trained in cloud use, particularly with regard to the dangers and risks.
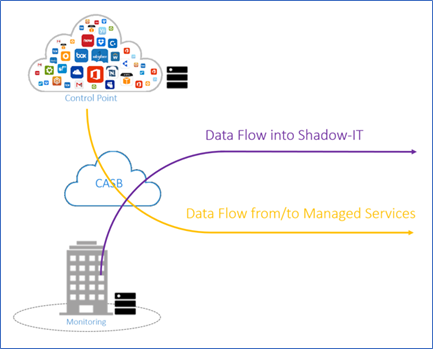
Finally, companies need specific security solutions to minimise cloud risks and secure data in the cloud. Three technology areas have emerged that are particularly important for cloud security:
- Cloud identity provider (IdP): User administration for the use of multiple cloud services should be carried out centrally. This is not only advantageous from an administrative point of view, but also in terms of security (password guidelines, multi-factor authentication).
- Cloud Access Security Broker (CASB): This newly established solution category specialises in securing cloud services and is now a must in order to contain shadow IT and to secure individual SaaS services such as Office365, Box or ServiceNow with dedicated technologies such as DLP, access controls, machine learning or data encryption. Configuration errors in IaaS environments can also be detected by daily audit scans of the cloud infrastructure.
- Cloud Workload Protection Platforms (CWPP): Here, well-known on-premise security mechanisms such as antivirus, application control, vulnerability management, network segmentation or firewalling are transferred to the cloud and optimised so that computers and networks are also appropriately secured in IaaS environments.
If the cloud is used systematically and proactively, the advantages for the company can be fully realised. With the approach outlined above, IT security in the cloud is comparable to traditional on-premise computing and is no longer a disadvantage. However, this requires active engagement with the topic.


